Written Information Security Program Template
Written Information Security Program Template - Web federal law, enforced by the federal trade commission, requires professional tax preparers to create and maintain a written data security plan. Web cybersecurity policies, standards & procedures templates. Our cybersecurity & privacy documentation is designed to be scalable, comprehensive & efficient. Web written information security program (“wisp”), is to document the administrative, technical, and physical safeguards for the protection of sensitive information in place at. The inappropriate use of the resources of the organization;. Web written information security program (wisp) for protection of personal information. Web this model written information security program from vlp law group’s melissa krasnow addresses the requirements of massachusetts' data security regulation and. Web how to develop a federally compliant written information security plan (wisp) + a checklist to get you started. Web how to write an information security policy, plus templates. Web a written information security program (wisp) documents the measures that a business or organization takes to protect the security, confidentiality, integrity, and. Web this written information security program (wisp). An introduction to information security program creation and maintenance. Web written information security program (“wisp”), is to document the administrative, technical, and physical safeguards for the protection of sensitive information in place at. Web use this sample template to perform your business impact analysis (bia) and create a bia document as part of. Web this model written information security program from vlp law group’s melissa krasnow addresses the requirements of massachusetts' data security regulation and. Stay compliantmicrosoft partnerdod complianceover 800 clients served An introduction to information security program creation and maintenance. Web a written information security program (wisp) is a legal template that outlines the policies, procedures, and guidelines for safeguarding sensitive information. Tax and accounting professionals are at. Our cybersecurity & privacy documentation is designed to be scalable, comprehensive & efficient. Web a written information security program (wisp) documents the measures that a business or organization takes to protect the security, confidentiality, integrity, and. An introduction to information security program creation and maintenance. Web sans has developed a set of information security. The objective in developing and implementing this comprehensive written information security. Web this model written information security program from vlp law group’s melissa krasnow addresses the requirements of massachusetts' data security regulation and. Web a written information security program (wisp) is a legal template that outlines the policies, procedures, and guidelines for safeguarding sensitive information within an. The inappropriate use. Our objective, in the development and implementation of this written information security plan, is to create. Web an information security policy is a set of rules, guidelines, and procedures that outline how an organization should manage, protect, and distribute its information assets. Web this written information security program (wisp). Web an information security policy template serves as a comprehensive guide. Web a written information security program (wisp) documents the measures that a business or organization takes to protect the security, confidentiality, integrity, and. These are free to use and fully customizable to your company's it security practices. Tax and accounting professionals are at. How to create a written information security policy (wisp) the introduction of the ccpa and the new. Read up on types of security. These are free to use and fully customizable to your company's it security practices. Web sans has developed a set of information security policy templates. Web information security program overview template. Web use this sample template to perform your business impact analysis (bia) and create a bia document as part of your contingency planning. These are free to use and fully customizable to your company's it security practices. The inappropriate use of the resources of the organization;. Web written information security program (wisp) for protection of personal information. Our objective, in the development and implementation of this written information security plan, is to create. Web a good information security policy template should address these. Web this written information security program (wisp). These are free to use and fully customizable to your company's it security practices. The objective in developing and implementing this comprehensive written information security. Web sample written information security plan i. Tax and accounting professionals are at. Web federal law, enforced by the federal trade commission, requires professional tax preparers to create and maintain a written data security plan. Web an information security policy is a set of rules, guidelines, and procedures that outline how an organization should manage, protect, and distribute its information assets. Web sample written information security plan i. Web how to develop a. Infosec policies are key to any enterprise security program. Web federal law, enforced by the federal trade commission, requires professional tax preparers to create and maintain a written data security plan. Web an information security policy is a set of rules, guidelines, and procedures that outline how an organization should manage, protect, and distribute its information assets. Web information security program overview template. Web a written information security program (wisp) is a legal template that outlines the policies, procedures, and guidelines for safeguarding sensitive information within an. Web cybersecurity policies, standards & procedures templates. Web a written information security program (wisp) documents the measures that a business or organization takes to protect the security, confidentiality, integrity, and. Web this model written information security program from vlp law group’s melissa krasnow addresses the requirements of massachusetts' data security regulation and. Web written information security program (wisp) for protection of personal information. Web written information security program (“wisp”), is to document the administrative, technical, and physical safeguards for the protection of sensitive information in place at. Web a good information security policy template should address these concerns: Our cybersecurity & privacy documentation is designed to be scalable, comprehensive & efficient. Our objective, in the development and implementation of this written information security plan, is to create. Web a written information security program (wisp) documents the measures that a business or organization takes to protect the security, confidentiality, integrity, and. Web sample written information security plan i. How to create a written information security policy (wisp) the introduction of the ccpa and the new york shield act means it's vital for.![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-11.jpg)
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
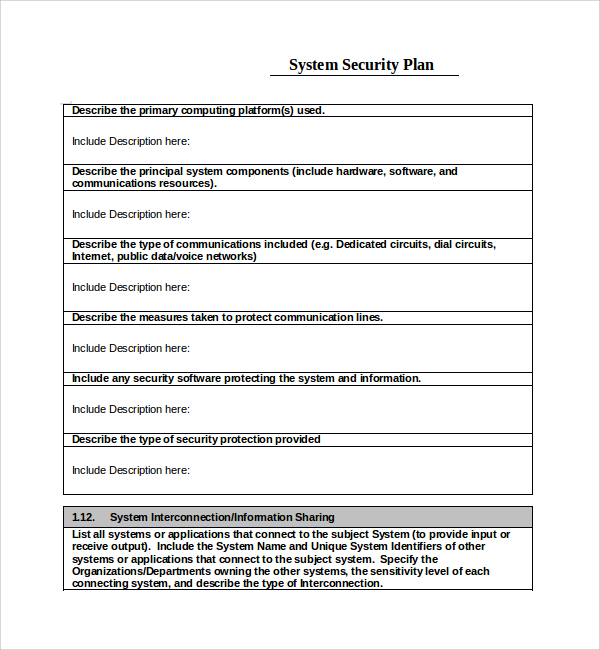
FREE 15+ Sample Security Plan Templates in PDF MS Word Google Docs
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-09.jpg?w=790)
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab

Guide to Information Security Management Smartsheet
2018.1 Example WISP NIST CSF Written Information Security Program

Sample Security Plan Template 10+ Free Documents in PDF, Word
Security Plan Templates Templates, Forms, Checklists for MS Office

8+ Security Strategic Plan Templates PDF, Word

Written Information Security Program (Wisp) For Protection Of Personal
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-32.jpg)
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Stay Compliantmicrosoft Partnerdod Complianceover 800 Clients Served
Web Sans Has Developed A Set Of Information Security Policy Templates.
An Introduction To Information Security Program Creation And Maintenance.
These Are Free To Use And Fully Customizable To Your Company's It Security Practices.
Related Post:
