User Authentication Database Design
User Authentication Database Design - Web there are two different authentication methods for connecting to sql server: This will translate your db design into users/roles that. Ensure that user feedback does not lead to compromises in data accuracy, consistency, and. Web make the design whatever you want to be, but in asp.net side implement your own membershipprovider. Web there are six types of database schemas: Do you think this is a proper database schema? Web i want to have a web service and a general authentication & authorization in one database so i must add a table for applicationname and add applicationid field. Web i am creating a user login system for my website and i need some help creating the database. Web in this tip we look at best ways to architect and design sql server security authentication. The web user initiates the interaction by logging in or registering. Web user authentication is the process of verifying the identity of a user accessing an application. Web in this tip we look at best ways to architect and design sql server security authentication. Web i want to have a web service and a general authentication & authorization in one database so i must add a table for applicationname and add. Web user authentication is the process of verifying the identity of a user accessing an application. So i far i have these 3 tables. Web the following is a relatively standard schema for a user table in a database. Web database design principles are essential to creating efficient, reliable, and scalable databases. Web there are two different authentication methods for. Ensure that user feedback does not lead to compromises in data accuracy, consistency, and. The web user initiates the interaction by logging in or registering. Web the database user is the identity of the login when it connects to a database. Do you think this is a proper database schema? This will translate your db design into users/roles that. Do you think this is a proper database schema? Web designing a robust database for an identity management system requires careful consideration of several critical factors, including data structure, scalability, data. Windows authentication requires a user to first. The objective of database security is to. Flat model, hierarchical model, network model, relational model, star schema, and snowflake schema. Web use case diagram for authentication system design. The database user can use the same name as the login, but that isn't required. The objective of database security is to. Web there are two approaches in which you can model rbac: Web there are six types of database schemas: So i far i have these 3 tables. A database created following these fundamental design principles. Web user authentication is the process of verifying the identity of a user accessing an application. Web make the design whatever you want to be, but in asp.net side implement your own membershipprovider. You can use this as a guide for when creating your. Web a simple model. Ensure that user feedback does not lead to compromises in data accuracy, consistency, and. The web user initiates the interaction by logging in or registering. Flat model, hierarchical model, network model, relational model, star schema, and snowflake schema. Web database security is the processes, tools, and controls that secure and protect databases against accidental and intentional. Naturally, we'll start with a table called users. Web database security is the processes, tools, and controls that secure and protect databases against accidental and intentional threats. Core rbac is designed by defining roles—groups of users with common. Web designing a robust database for an identity management system requires careful consideration of several critical factors, including data structure, scalability, data.. You can use this as a guide for when creating your own cutom authentication system. Web a simple model. Core rbac is designed by defining roles—groups of users with common. Ensure that user feedback does not lead to compromises in data accuracy, consistency, and. Web use case diagram for authentication system design. Web there are six types of database schemas: Core rbac is designed by defining roles—groups of users with common. Ensure that user feedback does not lead to compromises in data accuracy, consistency, and. This will translate your db design into users/roles that. Web there are two approaches in which you can model rbac: Web 4 data integrity. Web i am creating a user login system for my website and i need some help creating the database. Web user authentication is the process of verifying the identity of a user accessing an application. Ensure that user feedback does not lead to compromises in data accuracy, consistency, and. A database created following these fundamental design principles. The database user can use the same name as the login, but that isn't required. Web make the design whatever you want to be, but in asp.net side implement your own membershipprovider. Core rbac is designed by defining roles—groups of users with common. You can use this as a guide for when creating your own cutom authentication system. Web the following is a relatively standard schema for a user table in a database. Web there are two approaches in which you can model rbac: Windows authentication requires a user to first. Web the database user is the identity of the login when it connects to a database. Web there are six types of database schemas: The objective of database security is to. Web designing a robust database for an identity management system requires careful consideration of several critical factors, including data structure, scalability, data.
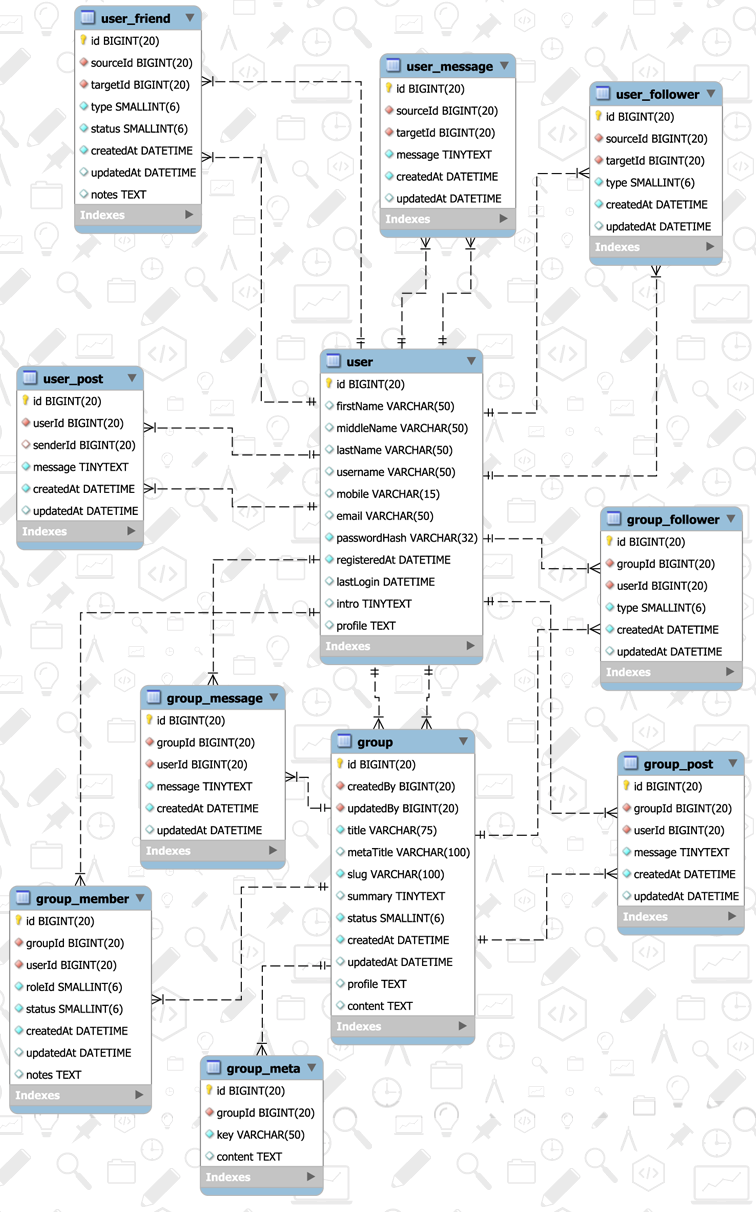
mysql Database design User table and relationships Database

Authentication via login interface verified via database Download
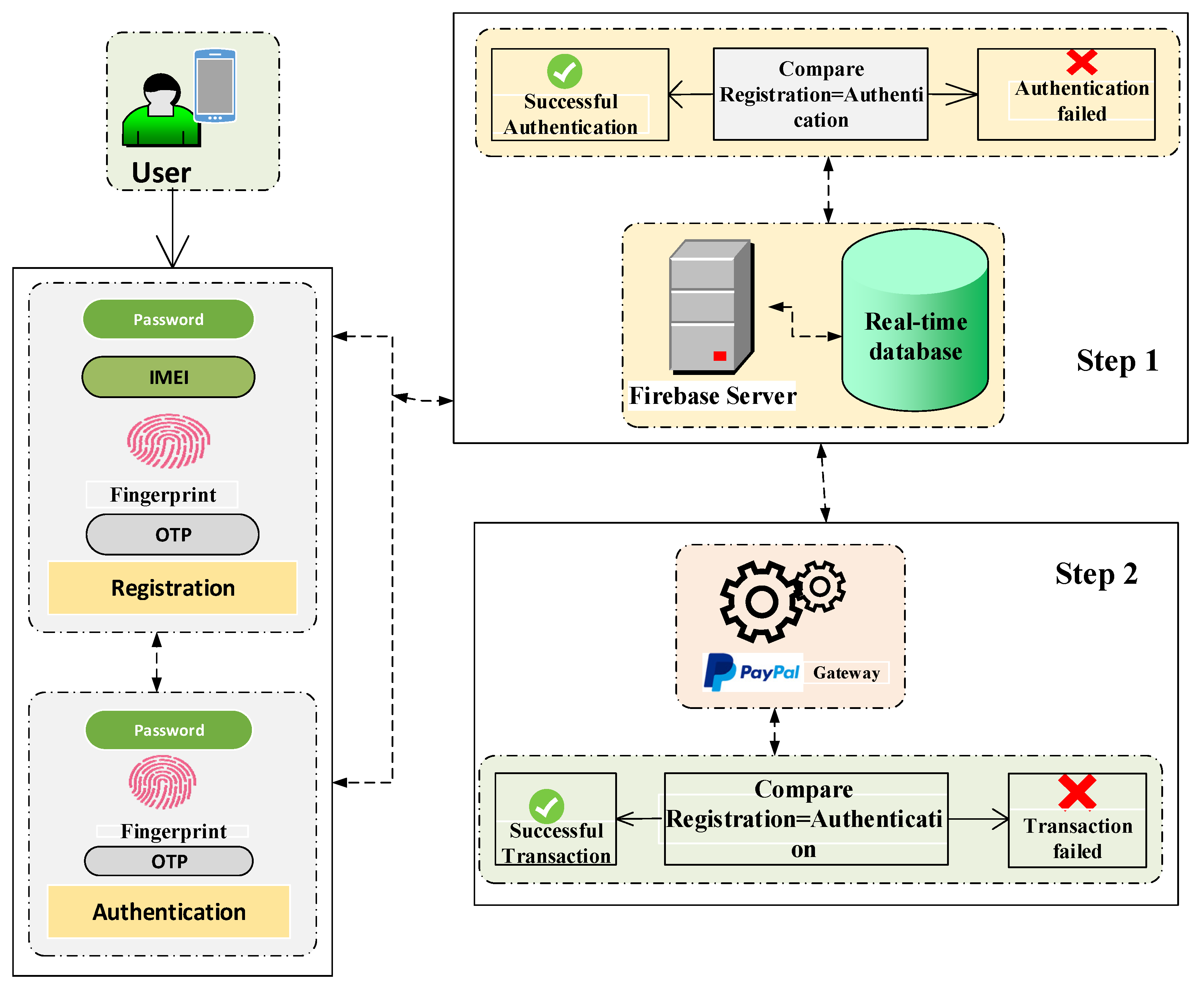
Electronics Free FullText Device IdentityBased User
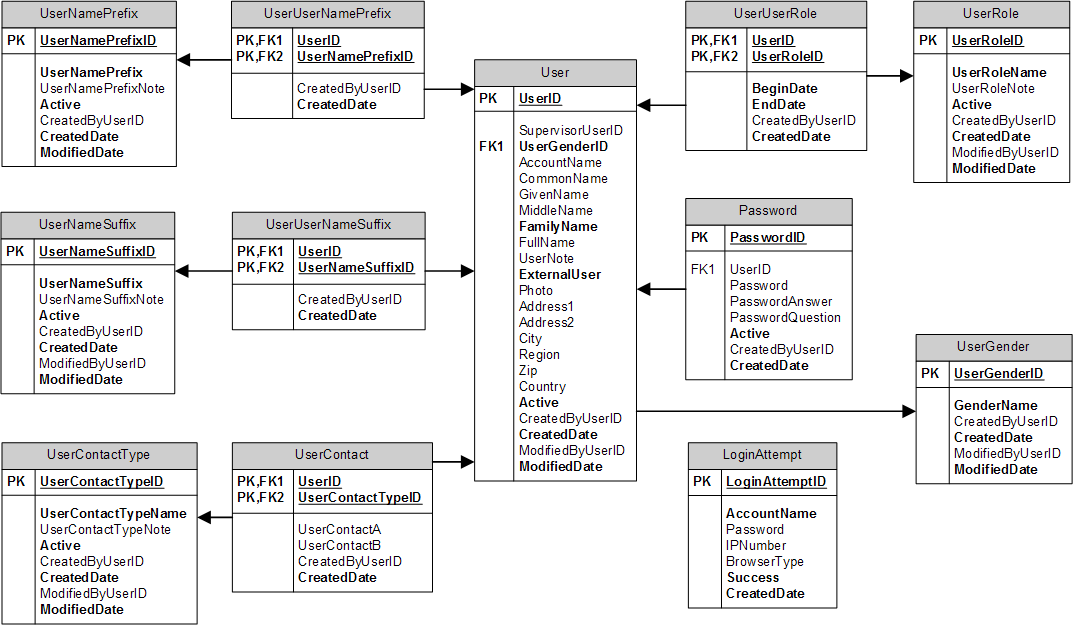
Database Schema for User Info, Authentication, Authorization
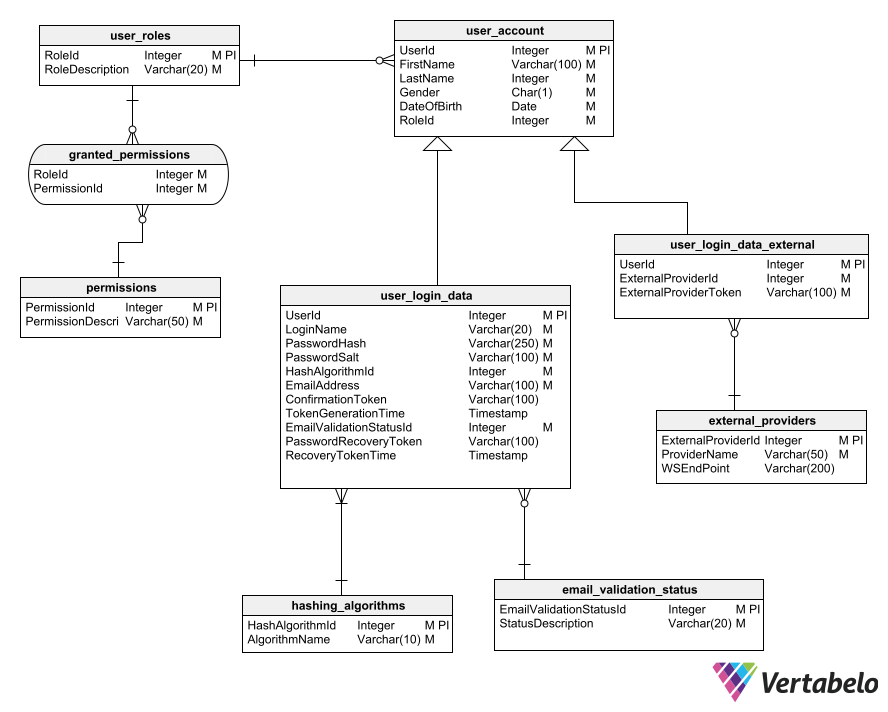
Best Practices for Designing a User Authentication Module Vertabelo

authentication Am I on the right track for a customer user login
Dbschema database connection authentication nativeopm
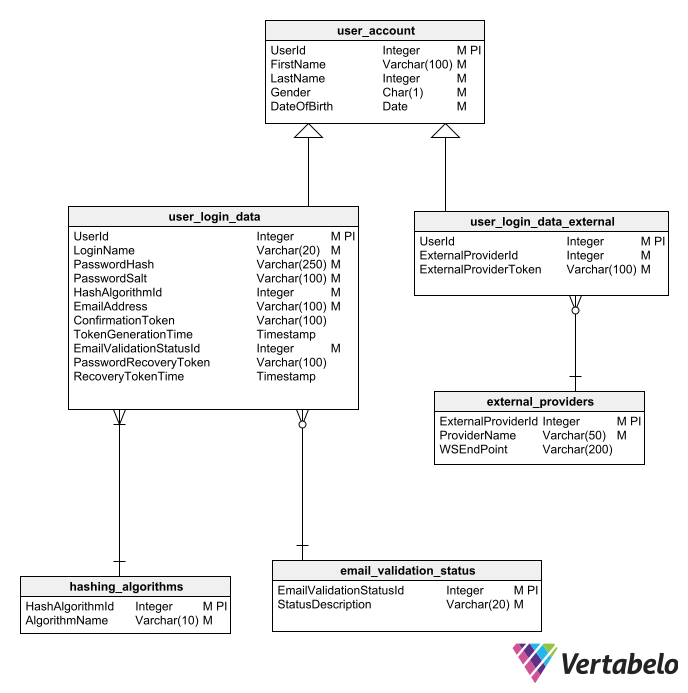
Best Practices for Designing a User Authentication Module Vertabelo

Password, Session, Cookie, Token, JWT, SSO, OAuth Authentication

sql General Database Design for Authorization & Authentication
Web A Simple Model.
Flat Model, Hierarchical Model, Network Model, Relational Model, Star Schema, And Snowflake Schema.
Web An Authentication Method Is How The User Submits Or Attests To Their Credentials.
Web Database Design Principles Are Essential To Creating Efficient, Reliable, And Scalable Databases.
Related Post: