Security Pattern
Security Pattern - Web as technology advances and develops, the need for strong and simple authentication mechanisms that can help protect data intensifies. Web windows at its core is an open and versatile os, and it can easily be locked down for increased security using integrated tools. This guide provides a te… The security patterns defined in these guides are. In addition, windows is constantly. Web learn about industry patterns that support security and can help you address common challenges in cloud workloads. 1.1 why do we need security patterns? The following security pattern describes. In the security engineering manifesto, we discussed that security is a systemic matter, and we should consider the environment in which the security. We are a dedicated team of professionals with solid expertise in the fields of cybersecurity, cryptography, microprocessors, security protocols,. All of the classical design patterns have different instantiations to fulfill some information security goal: Web as technology advances and develops, the need for strong and simple authentication mechanisms that can help protect data intensifies. Apis are the interface to external and internal users through which valuable business information is shared. Most importantly in that process, we note the. Security. The security patterns defined in these guides are. This guide provides a te… Web the fundamental security requirements that have to be addressed during design phase are authentication and authorization. Web windows at its core is an open and versatile os, and it can easily be locked down for increased security using integrated tools. I’ve been working in the security. Additionally, one can create a new design pattern to specifically achieve some security goal. Web the fundamental security requirements that have to be addressed during design phase are authentication and authorization. Therefore, it is vital for applications security architects. Web as technology advances and develops, the need for strong and simple authentication mechanisms that can help protect data intensifies. Web. All of the classical design patterns have different instantiations to fulfill some information security goal: Additionally, one can create a new design pattern to specifically achieve some security goal. Such as confidentiality, integrity, and availability. In the security engineering manifesto, we discussed that security is a systemic matter, and we should consider the environment in which the security. Web as. Web 29 rows 11.02 security architecture patterns. Most importantly in that process, we note the. Apis are the interface to external and internal users through which valuable business information is shared. Web available patterns (nist sp 800:53 framework) security pattern: The following security pattern describes. The security patterns defined in these guides are. Web within the ‘how to write a security pattern’ guide, we step through the process of constructing a security pattern. Web 29 rows 11.02 security architecture patterns. Web france was gripped by a sequence of coordinated railway attacks on friday, prompting speculation over the identity of actors who unleashed national travel chaos. The security patterns defined in these guides are. In addition, windows is constantly. Web within the ‘how to write a security pattern’ guide, we step through the process of constructing a security pattern. Web but for a brief time after the site was unveiled on monday, the system preprinted the voter’s name, address, birth date, driver’s license number and last. 1.4 industrial use of security. Web security patterns addresses the full spectrum of security in systems design, using best practice solutions to show how to integrate security in the broader. In this article we discuss how the evolution of design patterns has shaped the prevalent understanding of security patterns. In the security engineering manifesto, we discussed that security is a. Web windows at its core is an open and versatile os, and it can easily be locked down for increased security using integrated tools. Most importantly in that process, we note the. Web available patterns (nist sp 800:53 framework) security pattern: Therefore, it is vital for applications security architects. 1.1 why do we need security patterns? Most importantly in that process, we note the. We help creators of intelligent connected devices to design, implement and operate their systems with a sustainable security level. The primary objective of this architectural design is to conduct a comprehensive examination of the application programming interface (api) gateway. Web windows at its core is an open and versatile os, and it. 1.1 why do we need security patterns? Web windows at its core is an open and versatile os, and it can easily be locked down for increased security using integrated tools. All of the classical design patterns have different instantiations to fulfill some information security goal: Therefore, it is vital for applications security architects. The security patterns defined in these guides are. Web 29 rows 11.02 security architecture patterns. I’ve been working in the security industry for over 15 years and always struggled in finding clear processes for defining security. Osa it security architecture patterns are based on architectural overview diagrams depicting a certain information usage context. We help creators of intelligent connected devices to design, implement and operate their systems with a sustainable security level. Apis are the interface to external and internal users through which valuable business information is shared. In addition, windows is constantly. Most importantly in that process, we note the. Web france was gripped by a sequence of coordinated railway attacks on friday, prompting speculation over the identity of actors who unleashed national travel chaos on. Web within the ‘how to write a security pattern’ guide, we step through the process of constructing a security pattern. 1.4 industrial use of security. In this article we discuss how the evolution of design patterns has shaped the prevalent understanding of security patterns.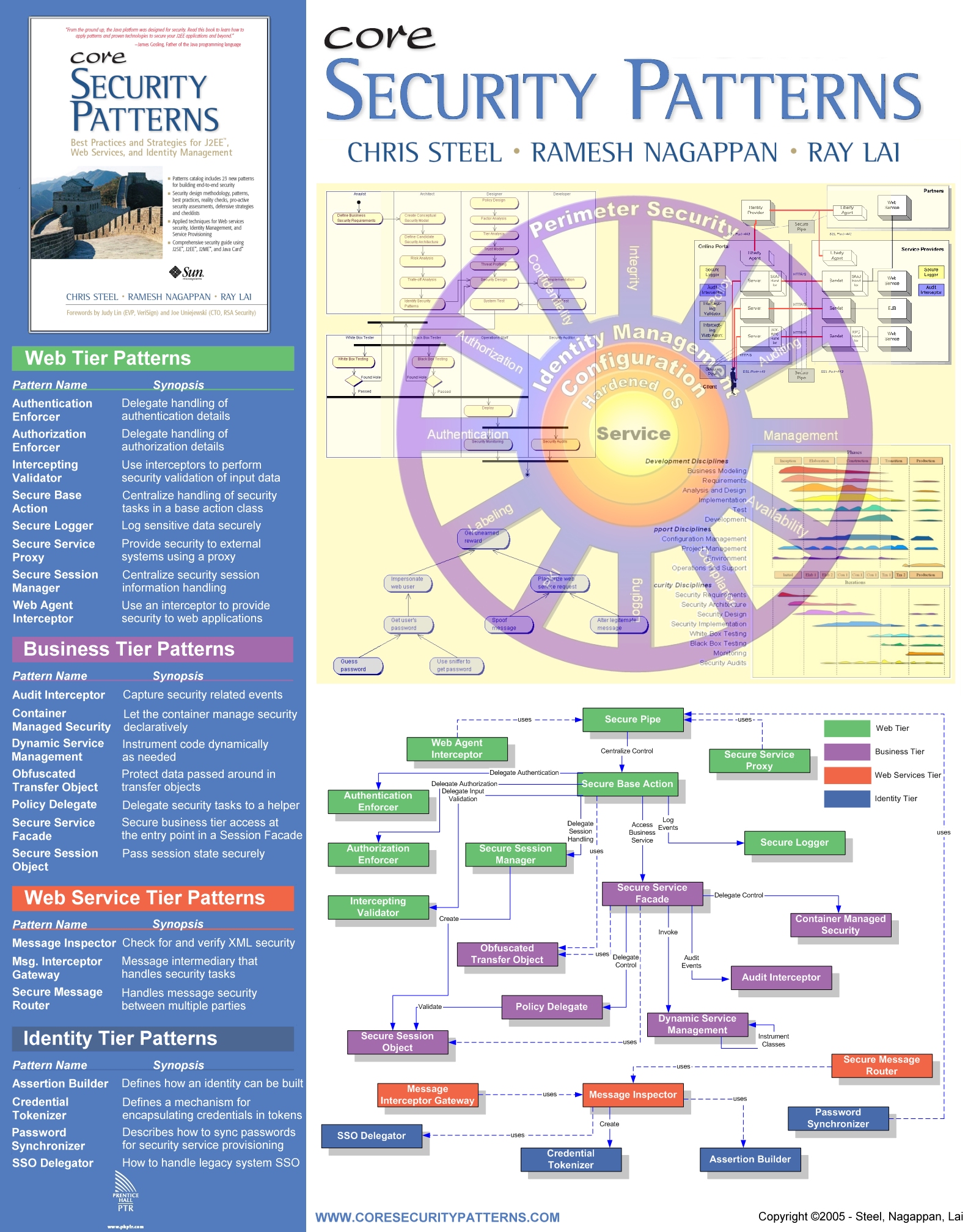
Core Security Patterns Ramesh Nagappan CISSP, Chris Steel CISSP

Security pattern (23738) Free EPS Download / 4 Vector
Security pattern 01 vector Free Vector / 4Vector
How to Write A Security Pattern Writing Patterns
How to Write A Security Pattern Service Mesh

Security Patterns How To Make Security Arch Easy To Consume
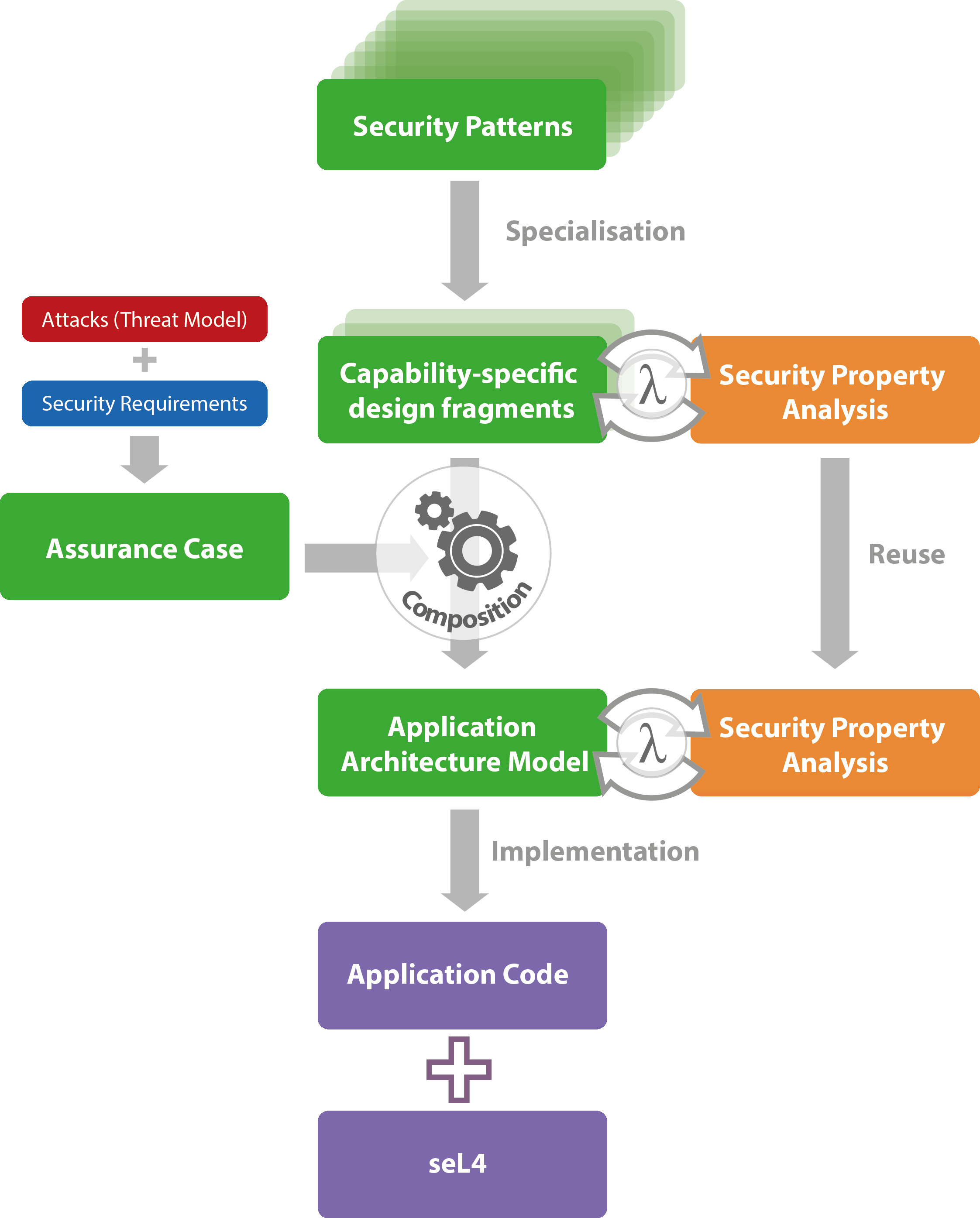
Secure Design using Security Patterns TS
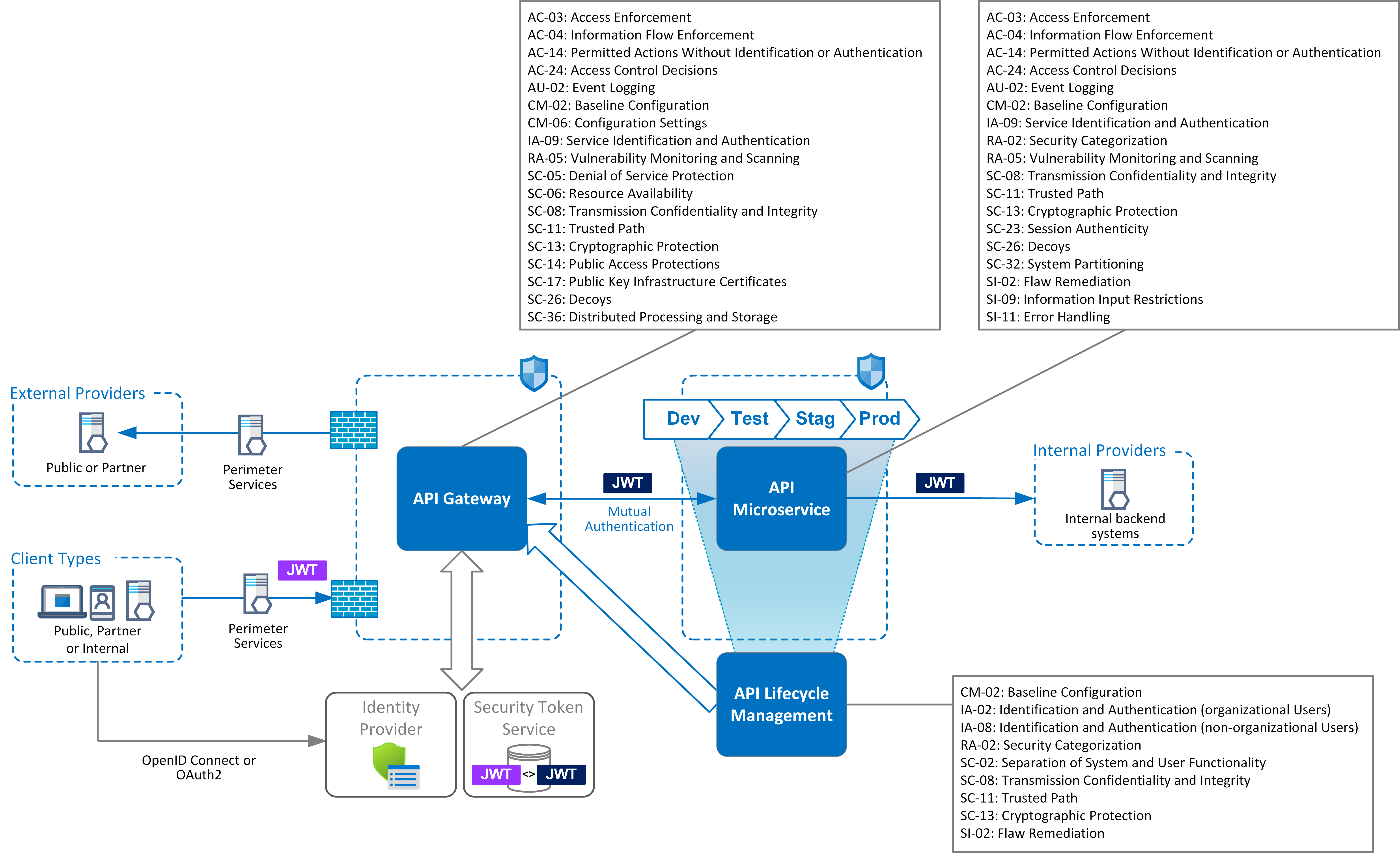
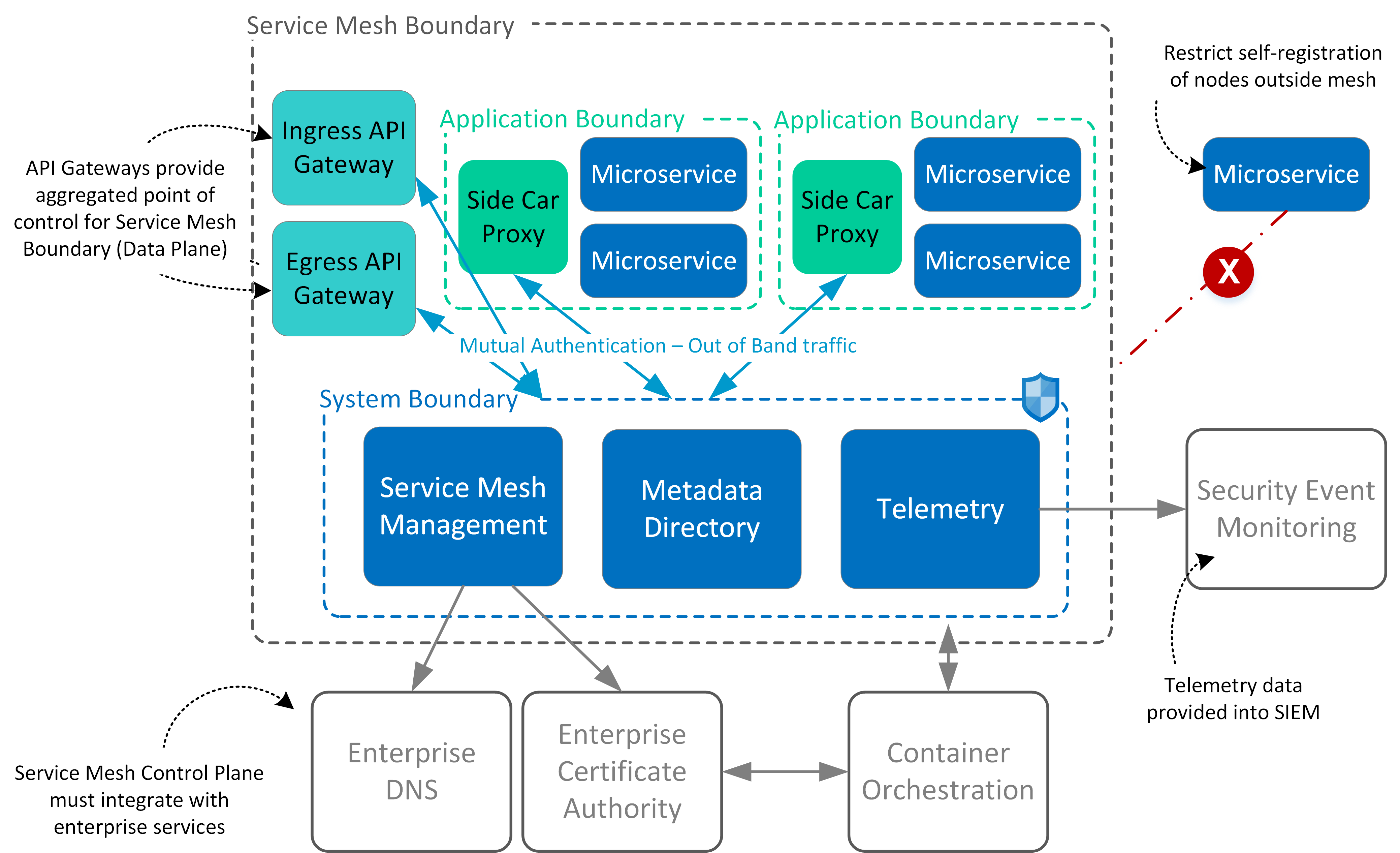
How to Write A Security Pattern API based Microservices

Mapping attack pattern to security patterns Download Scientific Diagram
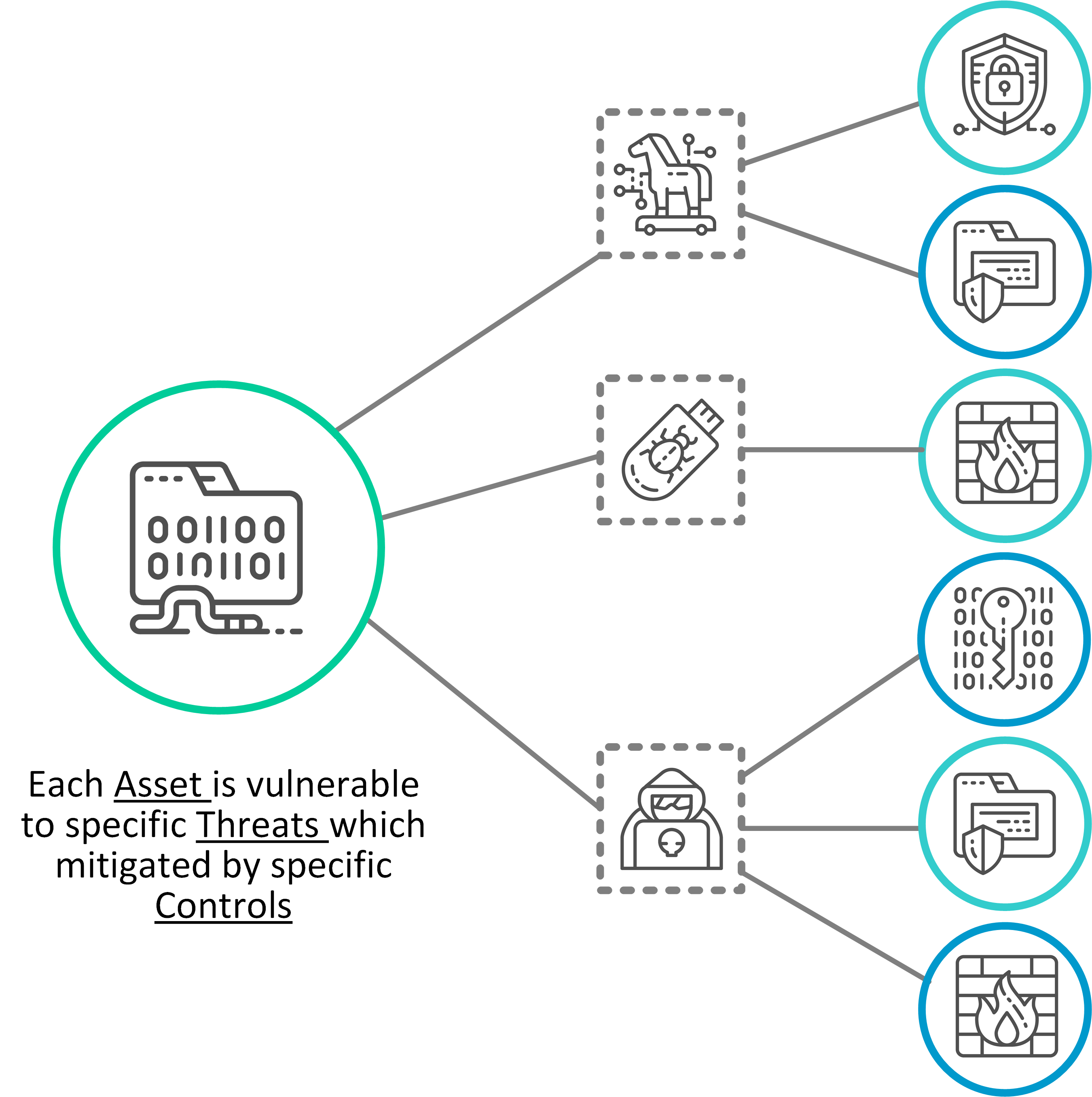
How to Write A Security Pattern Writing Patterns
Web But For A Brief Time After The Site Was Unveiled On Monday, The System Preprinted The Voter’s Name, Address, Birth Date, Driver’s License Number And Last Four.
Include A Brief Abstract Summary To The Pattern And Background To The Problem (In A Few Sentences).
Such As Confidentiality, Integrity, And Availability.
We Are A Dedicated Team Of Professionals With Solid Expertise In The Fields Of Cybersecurity, Cryptography, Microprocessors, Security Protocols,.
Related Post: