Ransomware Playbook Template
Ransomware Playbook Template - Web microsoft defender for cloud (azure) microsoft sentinel incident response. Web a ransomware attack by taking preventative actions (e.g., creating a backup of critical data) and developing and testing a ransomware incident response plan. Web the following diagram (figure 1) provides a visual representation of how ransomware can infect your networks and devices, highlighting the three main access vectors commonly. Web evaluate security control performance against baseline behaviors associated with the prestige ransomware. Web this comprehensive ransomware incident playbook guide shows you how to create an effective incident playbook to respond effectively to ransomware attacks. Download our free ransomware response playbook now. Containment is critical in ransomware incidents, prioritize accordingly. Supply chain attacks allow threat actors to infiltrate a service. Introduction to qualys ransomware risk assessment service. If under attack, quickly do the scoping and plan for containment. Web ransomware attacks require a unique approach to handling the associated incident response. Microsoft incident response team guide shares best practices for security teams and leaders. Web a ransomware attack by taking preventative actions (e.g., creating a backup of critical data) and developing and testing a ransomware incident response plan. Web detect, respond, and recover from ransomware incidents. The playbook. Download our free ransomware response playbook now. Web this playbook outlines response steps for handling ransomware incidents. Web a ransomware attack by taking preventative actions (e.g., creating a backup of critical data) and developing and testing a ransomware incident response plan. Web ransomware is a type of malicious attack where attackers encrypt an organization’s data and demand payment to restore. The playbook defines key stakeholders, processes, policies & prevention plans to defend your organization. Web ransomware is a type of malicious attack where attackers encrypt an organization’s data and demand payment to restore access. Web the following diagram (figure 1) provides a visual representation of how ransomware can infect your networks and devices, highlighting the three main access vectors commonly.. Introduction to qualys ransomware risk assessment service. Web this comprehensive ransomware incident playbook guide shows you how to create an effective incident playbook to respond effectively to ransomware attacks. Assess their security posture against a highly disruptive and. Web this playbook will outline indicators of compromise (ioc) that will be used to identify infected machines or malicious activity, as well. Here’s an example of how a ransomware. This toolkit provides the necessary resources to develop a comprehensive. Assess their security posture against a highly disruptive and. Microsoft incident response team guide shares best practices for security teams and leaders. Supply chain attacks allow threat actors to infiltrate a service. Actions you can take to lower the risk and impact of this kind of attack. This toolkit provides the necessary resources to develop a comprehensive. Ransomware investigate, remediate (contain, eradicate), and communicate in parallel! Download our free ransomware response playbook now. Supply chain attacks allow threat actors to infiltrate a service. Actions you can take to lower the risk and impact of this kind of attack. Web this playbook outlines response steps for handling ransomware incidents. Ransomware is a form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Introduction to qualys ransomware risk assessment service. Download our free ransomware. Web this playbook outlines response steps for handling ransomware incidents. The ransomware plybook is intended to provide a roadmap for organizations to secure themselves against this growing threat. Here’s an example of how a ransomware. Web this playbook will outline indicators of compromise (ioc) that will be used to identify infected machines or malicious activity, as well as response actions. Web ransomware attacks require a unique approach to handling the associated incident response. Here’s an example of how a ransomware. Web ransomware is a type of malicious attack where attackers encrypt an organization’s data and demand payment to restore access. Web detect, respond, and recover from ransomware incidents. Assess their security posture against a highly disruptive and. If under attack, quickly do the scoping and plan for containment. Supply chain attacks allow threat actors to infiltrate a service. Web ransomware is a type of malicious attack where attackers encrypt an organization’s data and demand payment to restore access. Web microsoft defender for cloud (azure) microsoft sentinel incident response. Microsoft incident response team guide shares best practices for. Web microsoft defender for cloud (azure) microsoft sentinel incident response. Web a ransomware attack by taking preventative actions (e.g., creating a backup of critical data) and developing and testing a ransomware incident response plan. Web review itsm.50.030 cyber security considerations for consumers of managed services 1 to protect your organization. Actions you can take to lower the risk and impact of this kind of attack. This toolkit provides the necessary resources to develop a comprehensive. Web ransomware attacks require a unique approach to handling the associated incident response. Web this playbook outlines response steps for handling ransomware incidents. Playbook for a ransomware attack. Web this playbook will outline indicators of compromise (ioc) that will be used to identify infected machines or malicious activity, as well as response actions to take to mitigate. The playbook defines key stakeholders, processes, policies & prevention plans to defend your organization. To serve as a ransomware incident response guide. Ransomware is a form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Assess their security posture against a highly disruptive and. Web qualys ransomware risk assessment playbook. These steps are based on the nist computer security incident handling guide (special publication 800. Microsoft incident response team guide shares best practices for security teams and leaders.
Free Ransomware Response Playbook ORNA

Malware Playbook Template

Ransomware Playbook Template Nist

Ransomware Playbook Template Nist

Ransomware Response Playbook Policy Template Banking and Fintech
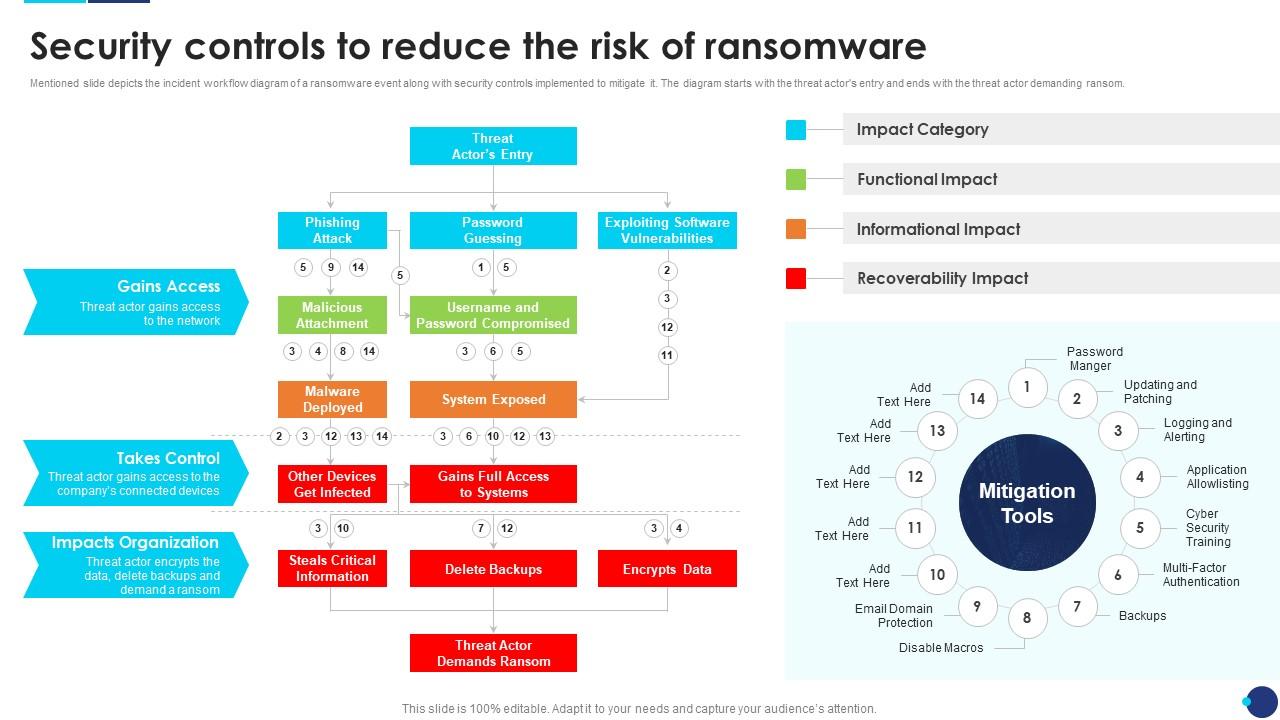
Incident Response Playbook Security Controls To Reduce The Risk Of

Quick Facts from the Ransomware Playbook Cyber Readiness Institute
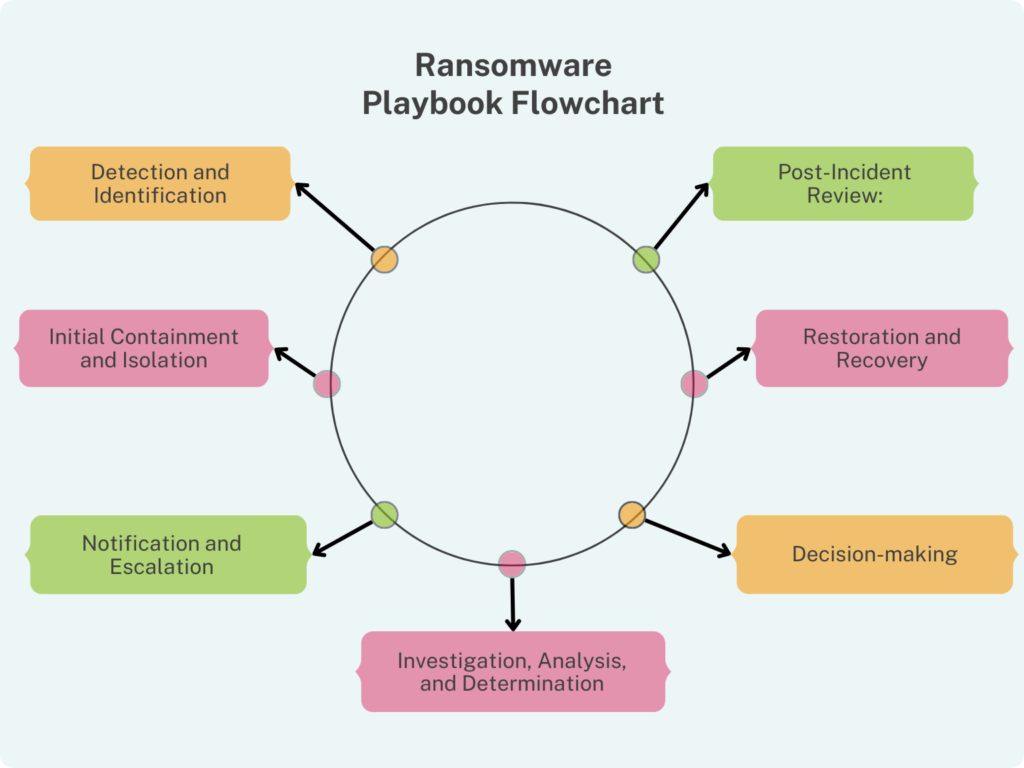
Ransomware Playbook Template
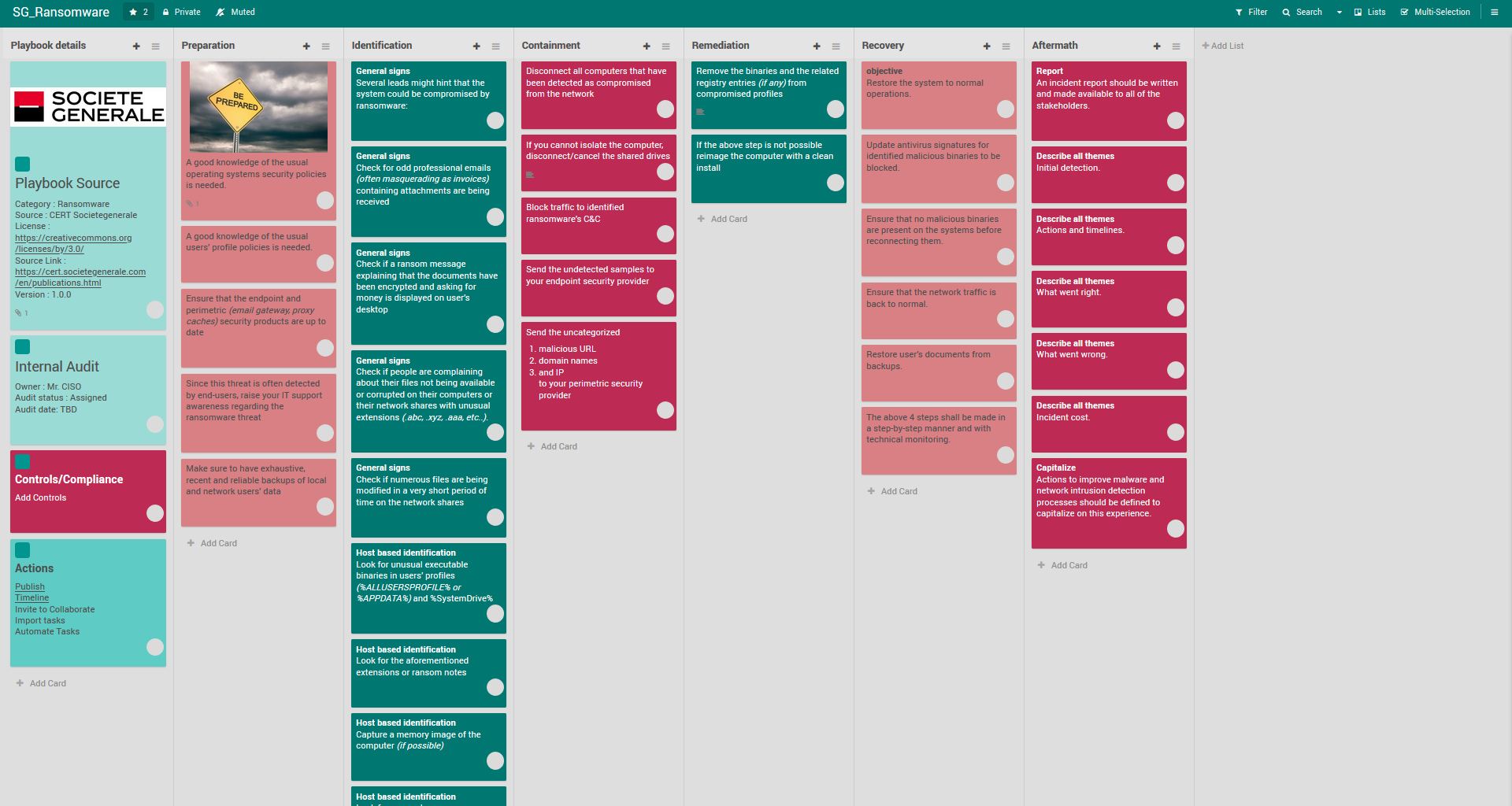
Ransomware Playbook Template
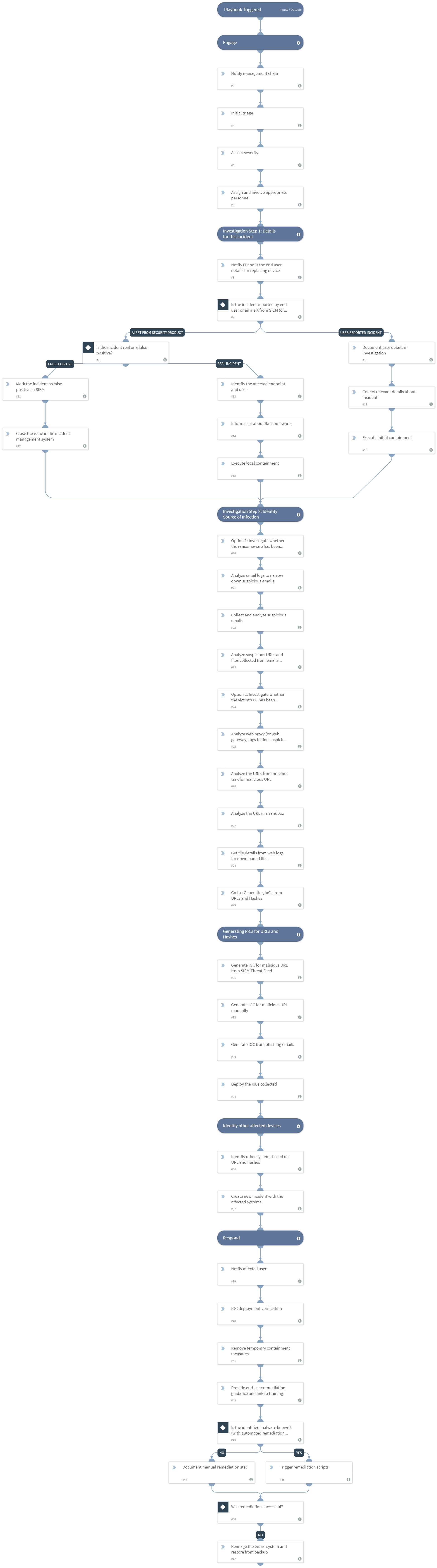
Ransomware Playbook Template Nist
If Under Attack, Quickly Do The Scoping And Plan For Containment.
Containment Is Critical In Ransomware Incidents, Prioritize Accordingly.
Ransomware Investigate, Remediate (Contain, Eradicate), And Communicate In Parallel!
Web This Comprehensive Ransomware Incident Playbook Guide Shows You How To Create An Effective Incident Playbook To Respond Effectively To Ransomware Attacks.
Related Post: