Fundamental Security Design Principles
Fundamental Security Design Principles - Web there has been an error, please try refreshing the page to rectify the error. Address possible abuse cases (e.g., how users may misuse the software). Web these principles should guide the security of your architecture, design choices, and operational processes. Web security principles and threat modeling. The open design security principle states that the implementation details of the design should be independent of the design itself, allowing the design to remain open while the implementation can be kept secret. These principles are inspired by the owasp development guide and are a set of desirable properties, behavior, design and implementation practices that we take into consideration when threat modeling at red hat. Web identifying and managing application security controls (ascs) or security requirements and security issues are essential aspects of an effective secure software development program. Build security considerations into the software requirements specification; Web here are five fundamental principles and practices that every organization needs to consider to get in front of and stay ahead of their current security challenges: After you set your strategy, drive actions by using the security checklist as your next step. Web these principles should guide the security of your architecture, design choices, and operational processes. If this error persists after several refreshes please allow some time to pass while we correct any problems or. One that doesn’t age out of usefulness or apply only to a few specific technologies and contexts; Create and enforce secure code guidelines. Web security principles. One that doesn’t age out of usefulness or apply only to a few specific technologies and contexts; Each primary group is described in detail in the sections that follow. Web security design principles are organized in a taxonomy with three primary groups, shown in figure 1. Web here are five fundamental principles and practices that every organization needs to consider. Start with the recommended approaches and justify the benefits for a set of security requirements. After you set your strategy, drive actions by using the security checklist as your next step. Each primary group is described in detail in the sections that follow. Web getting the most from the secure design principles. Web these principles should guide the security of. Web these principles are a powerful mental tool for approaching security: Web security principles and threat modeling. After you set your strategy, drive actions by using the security checklist as your next step. If this error persists after several refreshes please allow some time to pass while we correct any problems or. Create and enforce secure code guidelines. Build security considerations into the software requirements specification; One that doesn’t age out of usefulness or apply only to a few specific technologies and contexts; Web these principles should guide the security of your architecture, design choices, and operational processes. Start with the recommended approaches and justify the benefits for a set of security requirements. These principles are intended to. Web identifying and managing application security controls (ascs) or security requirements and security issues are essential aspects of an effective secure software development program. Web security design principles are organized in a taxonomy with three primary groups, shown in figure 1. Address possible abuse cases (e.g., how users may misuse the software). These principles are inspired by the owasp development. Web here are five fundamental principles and practices that every organization needs to consider to get in front of and stay ahead of their current security challenges: Build security considerations into the software requirements specification; Address possible abuse cases (e.g., how users may misuse the software). After you set your strategy, drive actions by using the security checklist as your. After you set your strategy, drive actions by using the security checklist as your next step. These principles are intended to help ensure that the networks and technologies which underpin modern life are designed and built securely. These principles are inspired by the owasp development guide and are a set of desirable properties, behavior, design and implementation practices that we. Web these principles are a powerful mental tool for approaching security: Start with the recommended approaches and justify the benefits for a set of security requirements. These principles are intended to help ensure that the networks and technologies which underpin modern life are designed and built securely. Each primary group is described in detail in the sections that follow. If. Web these principles should guide the security of your architecture, design choices, and operational processes. Web security principles and threat modeling. If this error persists after several refreshes please allow some time to pass while we correct any problems or. Start with the recommended approaches and justify the benefits for a set of security requirements. These principles are intended to. Web security principles and threat modeling. Web getting the most from the secure design principles. Start with the recommended approaches and justify the benefits for a set of security requirements. Web these principles are a powerful mental tool for approaching security: Address possible abuse cases (e.g., how users may misuse the software). After you set your strategy, drive actions by using the security checklist as your next step. If this error persists after several refreshes please allow some time to pass while we correct any problems or. The open design security principle states that the implementation details of the design should be independent of the design itself, allowing the design to remain open while the implementation can be kept secret. One that can be used for architecture, postmortem analysis, operations, and communication. Web here are five fundamental principles and practices that every organization needs to consider to get in front of and stay ahead of their current security challenges: Create and enforce secure code guidelines. Build security considerations into the software requirements specification; Web security design principles are organized in a taxonomy with three primary groups, shown in figure 1. One that doesn’t age out of usefulness or apply only to a few specific technologies and contexts; These principles are inspired by the owasp development guide and are a set of desirable properties, behavior, design and implementation practices that we take into consideration when threat modeling at red hat. These principles are intended to help ensure that the networks and technologies which underpin modern life are designed and built securely.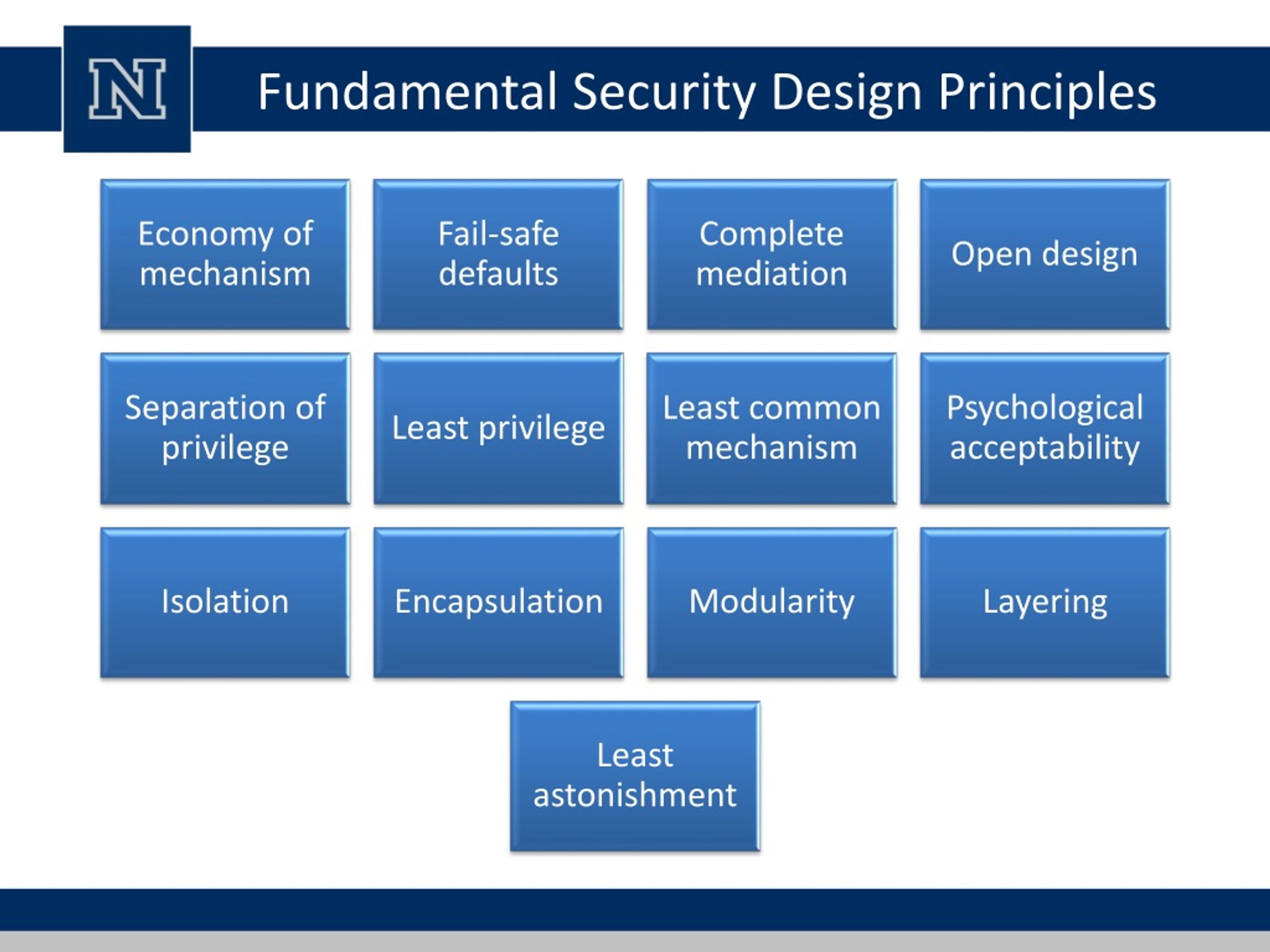
PPT Lecture 1 Overview PowerPoint Presentation, free download ID

Taxonomy of security design principles Download Scientific Diagram

SOLUTION Fundamental security design principles docx Studypool

PPT Information Security & Privacy PowerPoint Presentation, free
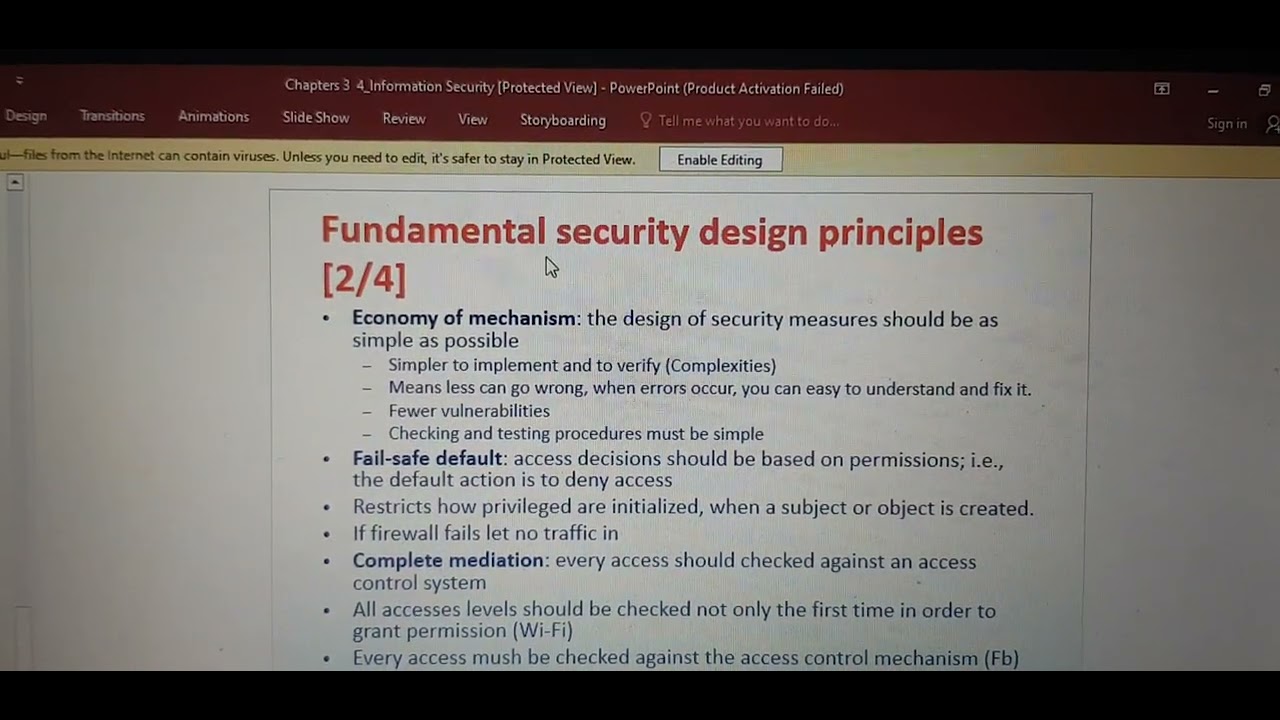
Fundamental security design principles YouTube

Fundamental Security Design Principles YouTube
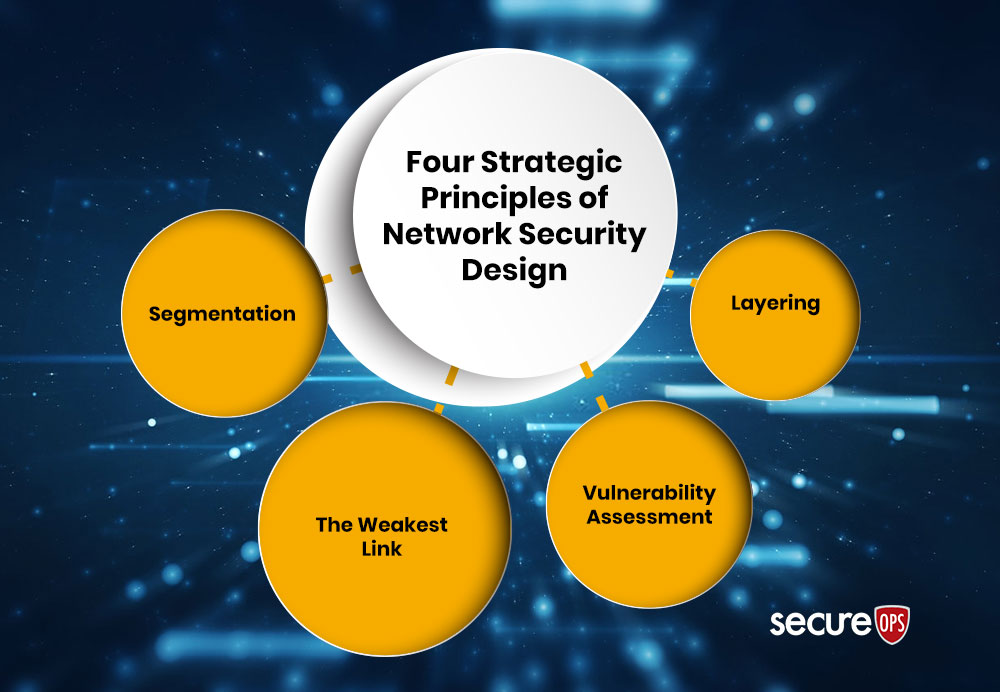
Four Strategic Principles of Network Security Design SecureOps
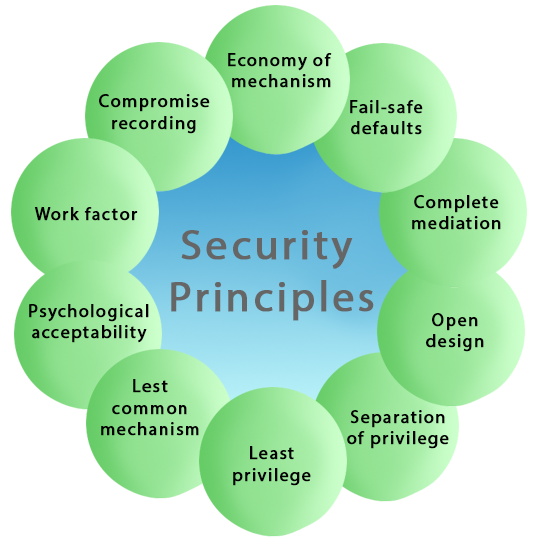
Various Types of Principles in Cyber Security FutureFundamentals
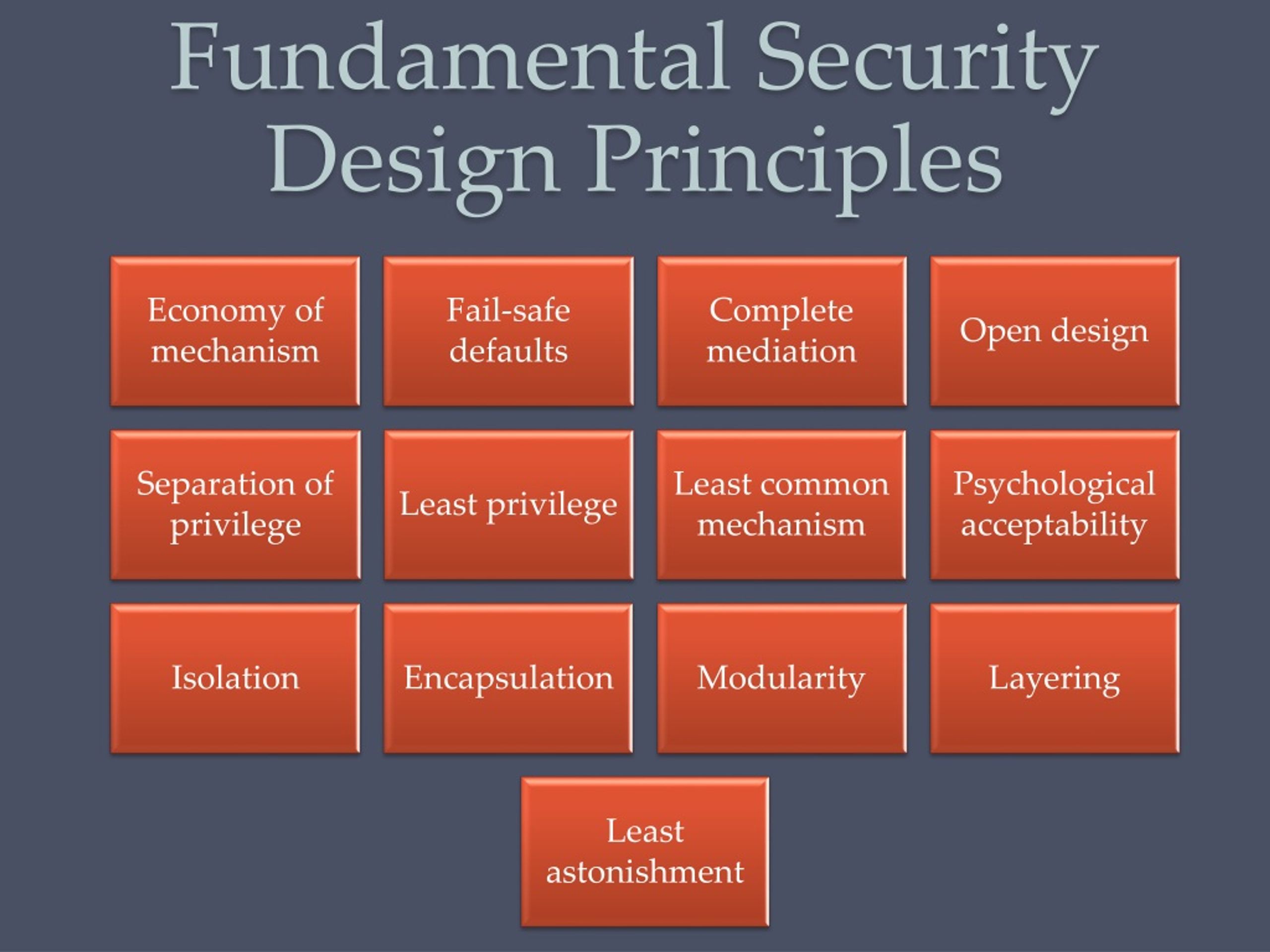
PPT Computer Security Principles and Practice Fourth Edition

Computer Security Principles and Practice Chapter 1 Overview
Web Identifying And Managing Application Security Controls (Ascs) Or Security Requirements And Security Issues Are Essential Aspects Of An Effective Secure Software Development Program.
Web These Principles Should Guide The Security Of Your Architecture, Design Choices, And Operational Processes.
Each Primary Group Is Described In Detail In The Sections That Follow.
Web There Has Been An Error, Please Try Refreshing The Page To Rectify The Error.
Related Post: