Data Access Patterns
Data Access Patterns - Data access operations are a common source of bottlenecks as they consume a significant portion of a system's memory. Web access patterns or query patterns define how the users and the system access the data to satisfy business needs. Create a preliminary cost estimation; Web in this article, we’ll discuss the differences between dao and repository patterns. Certain patterns of data access, and especially data updates, can exacerbate strain on the database. Web best practices for data layout and access patterns. Document the data access patterns. Create the dynamodb data model; Web the objective of this article is to give a overview of the main software data access patterns used in the software development industry, showing their features. Web an ‘access pattern’ refers to how your application reads and writes data. Identify your data access patterns; Web an ‘access pattern’ refers to how your application reads and writes data. It provides an abstraction layer between the application and the data storage, allowing for loose coupling and easier maintenance. Web in this post, we show you what the different data access patterns look like once you’ve selected a data isolation strategy. Web. This includes what kind of data it fetches, how often, and in what quantity. Web the data access object (dao) pattern separates the business logic of an application from the underlying data access mechanisms. Web these patterns concentrate on improving data access performance and resource utilizations by eliminating redundant data access operations. Certain patterns of data access, and especially data. Data access operations are a common source of bottlenecks as they consume a significant portion of a system's memory. Web these patterns concentrate on improving data access performance and resource utilizations by eliminating redundant data access operations. Provide a more detailed description of the access pattern. Collect and document information about the access patterns for the use case by using. Identify the use cases and logical data model; Provide a name for the access pattern. Data access operations are a common source of bottlenecks as they consume a significant portion of a system's memory. Provide a more detailed description of the access pattern. Web best practices for data layout and access patterns. Define a priority for the access pattern (high, medium, or low). Create a preliminary cost estimation; Provide a name for the access pattern. Web the data access object (dao) pattern separates the business logic of an application from the underlying data access mechanisms. Web the objective of this article is to give a overview of the main software data access. This document lists some patterns to avoid, with recommendations for alternatives. Certain patterns of data access, and especially data updates, can exacerbate strain on the database. Identify the use cases and logical data model; Identify your data access patterns; Define a priority for the access pattern (high, medium, or low). Certain patterns of data access, and especially data updates, can exacerbate strain on the database. Web in this post, we show you what the different data access patterns look like once you’ve selected a data isolation strategy. Collect and document information about the access patterns for the use case by using the following fields: Web in this article, we’ll discuss. Provide a name for the access pattern. This includes what kind of data it fetches, how often, and in what quantity. Web best practices for data layout and access patterns. Identify your data access patterns; Web an ‘access pattern’ refers to how your application reads and writes data. Web the data access object (dao) pattern separates the business logic of an application from the underlying data access mechanisms. Certain patterns of data access, and especially data updates, can exacerbate strain on the database. Web an ‘access pattern’ refers to how your application reads and writes data. This includes what kind of data it fetches, how often, and in. It provides an abstraction layer between the application and the data storage, allowing for loose coupling and easier maintenance. Web the objective of this article is to give a overview of the main software data access patterns used in the software development industry, showing their features. This document lists some patterns to avoid, with recommendations for alternatives. Create a preliminary. Web in this article, we’ll discuss the differences between dao and repository patterns. Web access patterns or query patterns define how the users and the system access the data to satisfy business needs. Provide a more detailed description of the access pattern. Provide a name for the access pattern. Certain patterns of data access, and especially data updates, can exacerbate strain on the database. Web best practices for data layout and access patterns. Create the dynamodb data model; This document lists some patterns to avoid, with recommendations for alternatives. Identify the use cases and logical data model; Define a priority for the access pattern (high, medium, or low). Web in this post, we show you what the different data access patterns look like once you’ve selected a data isolation strategy. Web these patterns concentrate on improving data access performance and resource utilizations by eliminating redundant data access operations. Identify your data access patterns; Document the data access patterns. It provides an abstraction layer between the application and the data storage, allowing for loose coupling and easier maintenance. Web the data access object (dao) pattern separates the business logic of an application from the underlying data access mechanisms.
Data Access Patterns. Three Tier Architecture

Data Access Object Design Pattern Introduction YouTube

Data Access Patterns Database Interactions in ObjectOriented
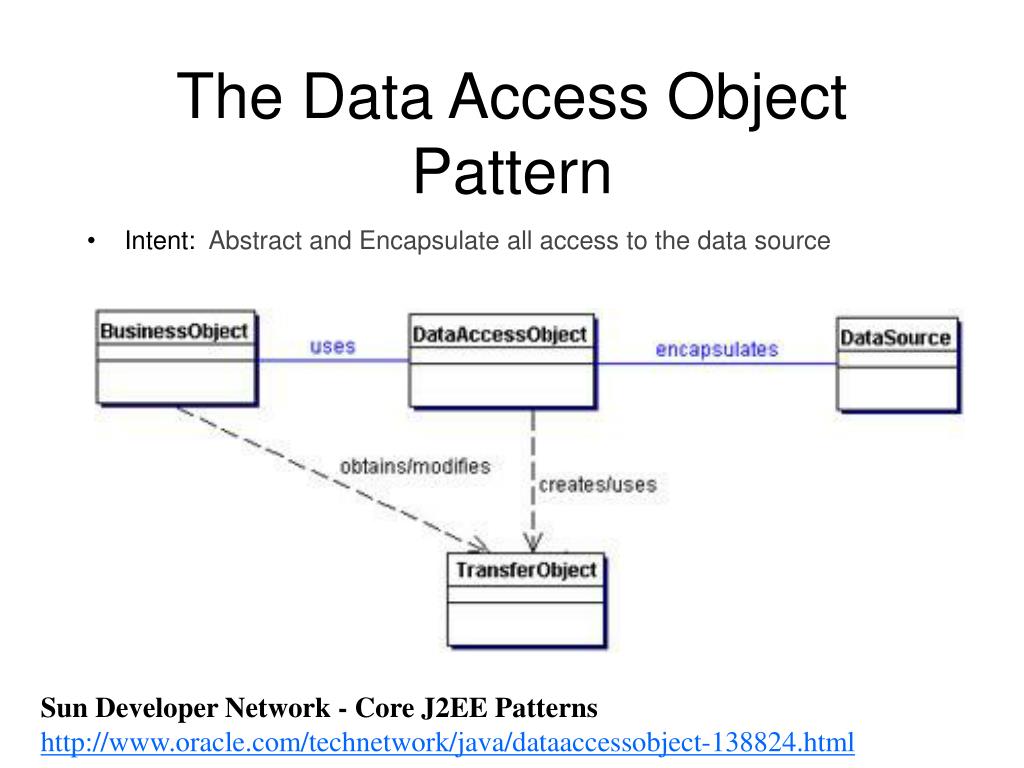
PPT Data Access Patterns PowerPoint Presentation, free download ID

Data access patterns of Montage workflow Download Scientific Diagram

Data Access Patterns Download Scientific Diagram

PPT Data Access Patterns PowerPoint Presentation, free download ID

Data access patterns for the row and column modules for the (5,3
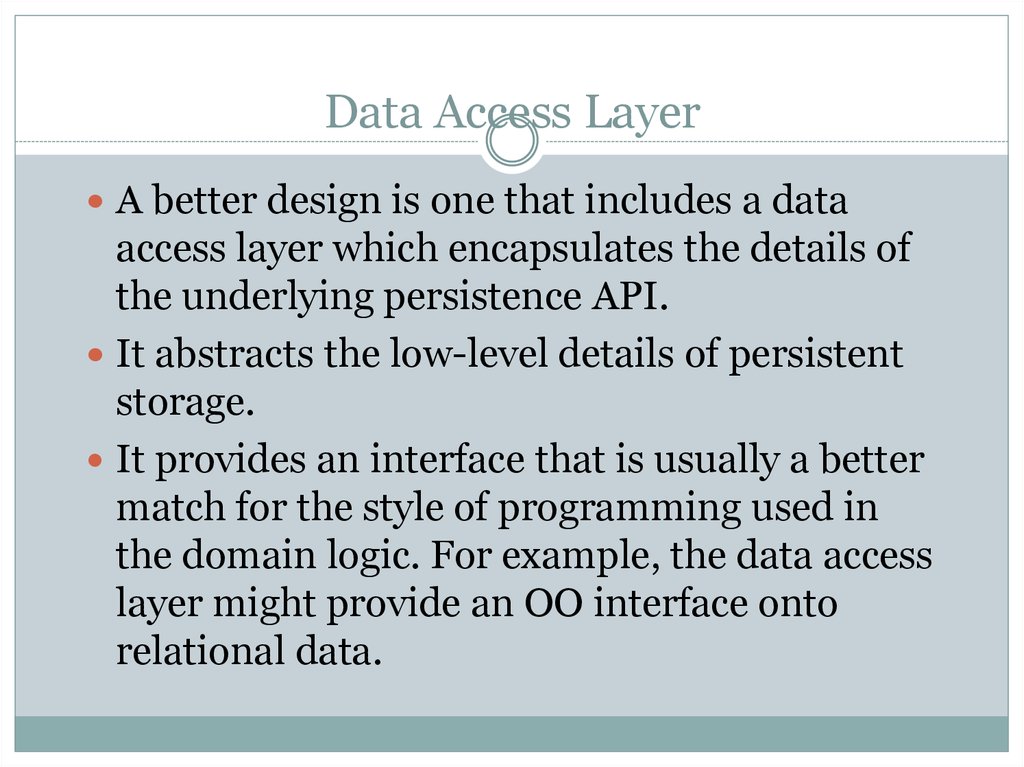
Data Access Patterns. Three Tier Architecture презентация онлайн

Common big data design patterns Packt Hub
Collect And Document Information About The Access Patterns For The Use Case By Using The Following Fields:
This Includes What Kind Of Data It Fetches, How Often, And In What Quantity.
Data Access Operations Are A Common Source Of Bottlenecks As They Consume A Significant Portion Of A System's Memory.
Create A Preliminary Cost Estimation;
Related Post: